Submitted by Jon Reed on
Hardly a week goes by in which we don't hear about a major breach in cyber security, be it stolen credit card data from a major retailer like Target or Home Depot, to leaked personal data, like the celebrity photo leak on iCloud or the Sony Pictures hack. We've all heard about stolen identities and the nightmare the victims go through to get them back, constant attempts of corporate espionage, and cases of private citizens being surveilled under dubious circumstances and cyber stalking and bullying dramas seem to be a staple of both the Lifetime channel and the local news. Unfortunately this sort of behavior is here to stay, at least for the foreseeable future.
The more personal information we put on our devices for the sake of convenience, the more susceptible we become to cyber-crime. The best way to protect yourself is to stay abreast of the latest security developments, keep your devices updated and use all measures that are available to you.
Here are seven steps to take right now to better protect yourself and your data:
1. Use Touch ID and a passcodeThis may be stating the obvious, but it can't be stressed enough. This is your first line of defense; not only will it block thieves from getting into your iPhone and your personal information, but it will stop friends from setting your background to obscene images as well.
Newest iPhone FAQs
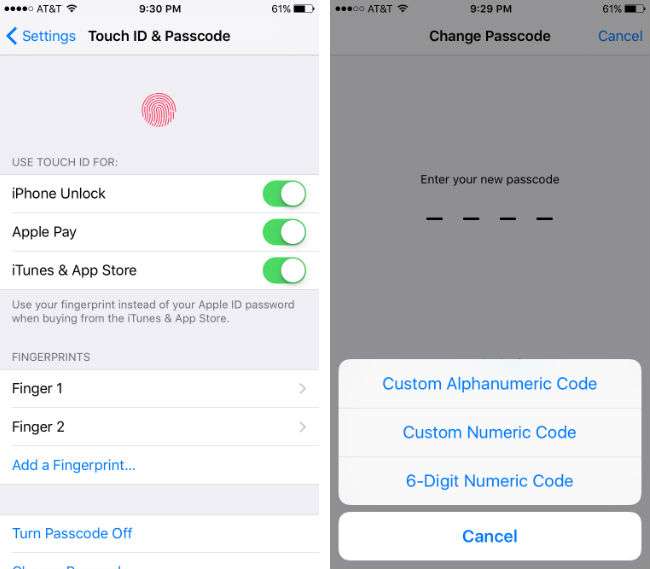
Touch ID should be used everywhere possible, as it is a very strong biometric security feature. According to Apple, it uses the touch sensor to create a mathematical representation of your fingerprint (not an image that could be stolen) that is encrypted and protected by a key that is only accessible to the Secure Enclave, a specialized security architecture included on your device's chip. The Secure Enclave can not be accessed by iOS or any other app, so your fingerprint data can never be uploaded to iCloud or any other Apple servers. You can activate your Touch ID for unlocking your iPhone, Apple Pay and for iTunes and the App Store in Settings -> Touch ID & Passcode. There are many other third party apps that can use Touch ID as well, including PayPal and Discover among others.
You should also make your passcode more secure by changing it from a 4 digit code to a 6 digit code or better yet, a strong alphanumeric code. While it may be annoying to have to type in a long passcode, as long as you are using Touch ID you will only have to do it if you restart your iPhone, go 48 hours without unlocking your device, or when you fail the Touch ID authentication several times in a row (which could happen with a dirty or wet sensor). If you have extremely sensitive data on your phone, you can also have your iPhone erase all of its data after 10 failed passcode attempts. This can be toggled on in Settings -> Touch ID & Passcode as well.
2. Lock Screen privacy
Even with Touch ID activated, there is still a period of vulnerability between when you put your phone down and when the Lock Screen activates. You can set the Auto-Lock time in Settings -> General -> Auto-Lock. The Lock Screen itself has its share of vulnerabilities as well - both Notifications and the Control Center can be accessed from it. Airplane Mode can be turned on from the Control Center, which would make it impossible to track with Find My iPhone. To avoid this, disallow access to the CC on the Lock Screen via Settings -> Control Center.
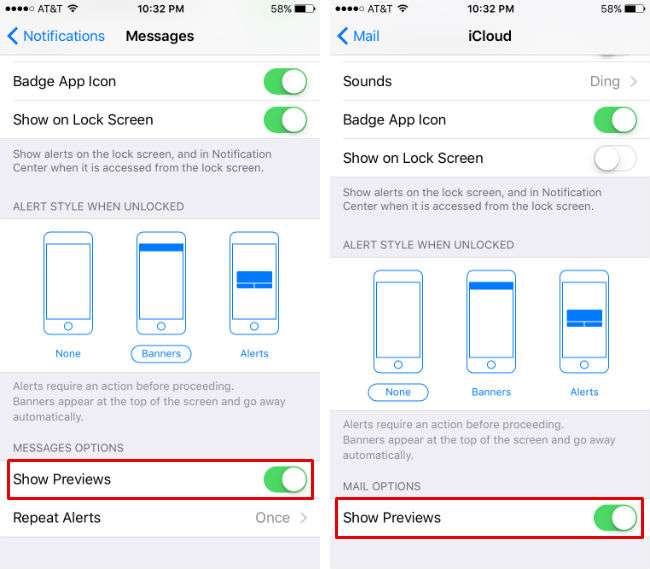
The contents of messages and emails will also display on the Lock Screen, possibly leaking information to prying eyes. Turn both of these off in Settings -> Notifications -> Messages and Settings -> Notifications -> Mail by toggling "Show Previews" to off. This way you will still be notified that a message or email has arrived, but no information will be displayed on the Lock Screen. You can also turn Notifications View off in Settings -> Touch ID & Passcode to block them completely.
Siri can also be used from the Lock Screen to obtain private information. Stop her from singing by toggling her off in Settings -> Touch ID & Passcode. You might consider turning off Wallet as well, though using a credit card from your Wallet requires Touch ID.
3. Find My iPhone
This is a no-brainer. Countless people have tracked down stolen iPhones with this feature, the author included. Of course it is also helpful for lost iPhones as well. With Find My iPhone you can have the phone flash and make a sound if it is misplaced somewhere, you can remotely lock it and have a message displayed on the screen if it has been lost or stolen, and you can even completely wipe the phone remotely if you have really sensitive material on it (though you won't be able to track it after doing so). Make sure you set it up.
4. Limit Location Services
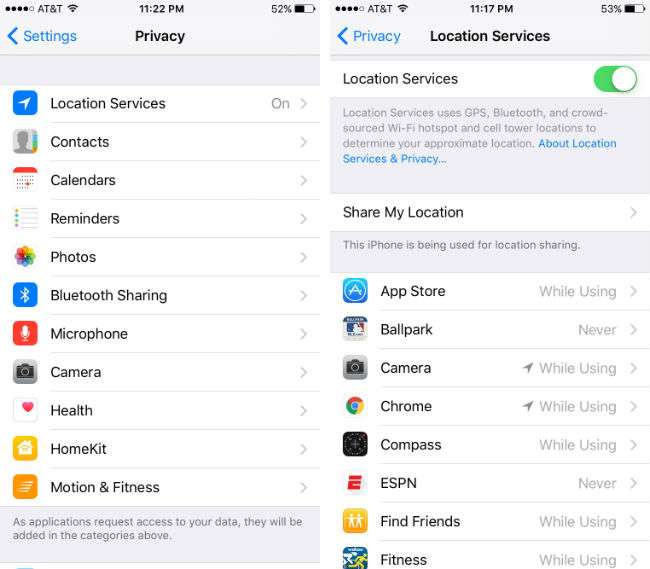
Apps constantly want to know where you are (data gathering for marketing purposes is a huge industry), and Location Services will tell them if you allow it. Don't, if it isn't necessary. Obviously you don't want to shut off location services for apps like Waze, but perhaps ESPN doesn't need to know where you are at all times. You can pick and choose which apps to give access to your whereabouts in Settings -> Privacy -> Location Services. While you are in Privacy, take a look through some of the other categories. Do you want a bunch of apps having access to your iPhone's microphone? You can limit access to Photos, Camera, Calendar, Contacts, HomeKit, Health and Reminders here as well.
5. Two-factor authentication
Two-factor authentication for your Apple ID is built into iOS 9 and OS X El Capitan to add an extra layer of security, ensuring that your data can only be accessed by you. With this security feature activated, whenever you enter your Apple ID on a new device, a six digit verification code will be sent to one of your other trusted devices. You use this code to complete your sign in instead of answering security questions. This way, even if somebody has your Apple ID and password, they won't be able to sign into your account. You won't need the security code again for that device unless you sign out. To further protect your photos, documents, credit card information and other data, consider activating two-factor authentication.
6. Internet privacy
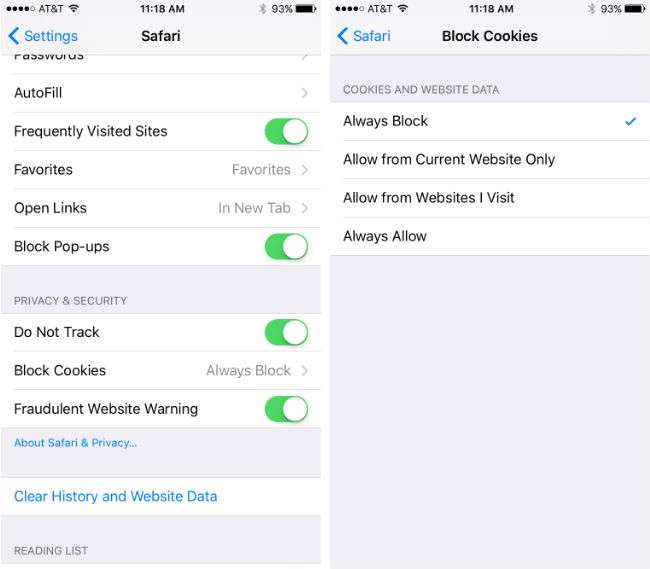
Your online activity is a big source of data that could potentially be compromised if somebody gets into your iPhone's browser. Not only that, but websites can track your activity with cookies and even capture your logins as well, so it is a good idea to enable all of your browser's security settings and keep it clean. You can tweak Safari's privacy settings in Settings -> Safari. Block cookies, turn on "Do Not Track," and turn off "Frequently Visited Sites" and "Safari Suggestions" to limit the amount of information sent to Apple and other websites. You can also clear your history here, which is a good thing to do from time to time. Limit Safari's access to Location Services, Photos, Contacts and others under Settings -> Privacy. You should also consider using Safari's private browsing feature, which will automatically delete history, cookies and any other cached data at the end of your session.
Internet browsing while on a public Wi-Fi network, such as at a coffee shop or hotel, can also be a risky venture, especially since you don't know how secure the network is. Data thieves can easily launch man-in-the-middle attacks to gain access to your private information. Consider using a virtual private network (VPN) to tunnel your information to a secure remote server. There are many free and paid VPN apps in the App Store such as TunnelBear, OpenVPN and Betternet among others.

7. Use a password manager
There are so many apps and websites that the average person logs into on a daily basis that it is nearly impossible to have a strong, unique password for each. Many resort to reusing passwords simply for convenience, which creates a major vulnerability. If your Netflix password is stolen along with your email address, a data thief can then try the combination on every other service you log into... bad news if you use the same password elsewhere. Use a password manager to ensure that you have strong, unique passwords for every login you have. For instance, LastPass, one of the more popular managers, keeps all of your passwords secure and uses them to log you in to your various sites and services. It can even use Touch ID to sign you in. You only need to remember one password - the LastPass login. It is a simple step that you should take to greatly improve your security.
After taking these steps to improve your privacy and security, make sure you keep up to date with new security trends, as this is a constantly escalating battle. What seems to be a foolproof security measure one month may be compromised and rendered obsolete the next, so you need to remain vigilant to keep your data protected.
